Become a Certified Cybersecurity Analyst
Learn and develop processes and tools to protect systems, networks, and programs from digital malicious attacks.





What you will learn:
- Understanding the significance of cybersecurity
- Types of cyber threat
- Network basics
- Installations and setup of all tools required in course of study.
- Networking protocols (TCP/IP, DNS, HTTP/HTTPS)
IP Addressing and Subnetting
- Open Source Intelligence (OSINT)
Passive Information Gathering
Active Information Gathering
DNS Enumeration
WHOIS Data Collection
Port Scanning Techniques
Service Enumeration
Vulnerability Scanning
Banner Grabbing
SNMP Enumeration
Privilege Escalation
Backdoors and Logic Bombs
Rootkits and Trojans
Post-Exploitation Activities
Web Server Enumeration
Web Application Vulnerabilities
Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
SQL Injection Basics
Firewall Evasion Methods
Honeypots and Honeynets
Packet Fragmentation
Protocol Tunneling
Spoofing and Masquerading
Encrypted Attacks
Symmetric Key Cryptography
Asymmetric Key Cryptography
Public Key Infrastructure (PKI)
Secure Key Exchange
Applications of Cryptography
Wireless Network Basics
Wi-Fi Security Protocols (WEP, WPA, WPA2, WPA3)
Wireless Network Authentication Methods
Wireless Access Point (AP) Security
Rogue Access Point Detection
Required Tools
Accelerator
Launch your Tech, Digital or Creative career fast with our intensive, hands-on training.
- 8 weeks training
- Choose from in-person or online practical training
- Tackle milestone projects
- Build a strong portfolio
Nest
Take your Tech, Digital or Creative career to the next level with everything in Accelerator, plus dedicated career support.
- We’ll help you craft a winning CV
- Optimize your LinkedIn profile
- Professional photographer’s headshot for your LinkedIn profile
- Master interview skills
- Get an internship placement at one of 100+ partner companies.
With NEST, you get everything you need to succeed!



What you will learn:
- Understanding the significance of cybersecurity
- Types of cyber threat
- Network basics
- Installations and setup of all tools required in course of study.
- Networking protocols (TCP/IP, DNS, HTTP/HTTPS)
IP Addressing and Subnetting
- Open Source Intelligence (OSINT)
Passive Information Gathering
Active Information Gathering
DNS Enumeration
WHOIS Data Collection
Port Scanning Techniques
Service Enumeration
Vulnerability Scanning
Banner Grabbing
SNMP Enumeration
Privilege Escalation
Backdoors and Logic Bombs
Rootkits and Trojans
Post-Exploitation Activities
Web Server Enumeration
Web Application Vulnerabilities
Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
SQL Injection Basics
Firewall Evasion Methods
Honeypots and Honeynets
Packet Fragmentation
Protocol Tunneling
Spoofing and Masquerading
Encrypted Attacks
Symmetric Key Cryptography
Asymmetric Key Cryptography
Public Key Infrastructure (PKI)
Secure Key Exchange
Applications of Cryptography
Wireless Network Basics
Wi-Fi Security Protocols (WEP, WPA, WPA2, WPA3)
Wireless Network Authentication Methods
Wireless Access Point (AP) Security
Rogue Access Point Detection
Required Tools
Accelerator
Launch your Tech, Digital or Creative career fast with our intensive, hands-on training.
- 8 weeks training
- Choose from in-person or online practical training
- Tackle milestone projects
- Build a strong portfolio
Nest
Take your Tech, Digital or Creative career to the next level with everything in Accelerator, plus dedicated career support.
- We’ll help you craft a winning CV
- Optimize your LinkedIn profile
- Professional photographer’s headshot for your LinkedIn profile
- Master interview skills
- Get an internship placement at one of 100+ partner companies.
With NEST, you get everything you need to succeed!
Upcoming Course Start Date
| Location | Start Date | Path | Schedule | Length | Tuition Fee | Status |
|---|---|---|---|---|---|---|
| Ikeja | August 5, 2024 | Accelerator | Weekdays or Weekends | 8 Weeks | N200,000 | Open |
| Online | August 5, 2024 | Accelerator | Weekdays or Weekends | 8 Weeks | N200,000 | Open |
Upcoming Course Start Date
| Location | Start Date | Path | Tuition Fee | Schedule | Status |
|---|---|---|---|---|---|
| Ikeja | August 5, 2024 | Accelerator 8 Weeks |
N200,000 | Weekdays or Weekends | Open |
| Online | August 5, 2024 | Accelerator 8 Weeks |
N200,000 | Weekdays or Weekends | Open |
Where Torilo grads. get hired
























Ready to start your Tech, Design,
Digital or Data journey?
Take the next step and speak to our admissions team. Book a 15-minute chat to ask questions and learn more about our programs.
Where Torilo grads. get hired
























Ready to start your Tech, Design, Digital or Data journey?
Take the next step and speak to our admissions team. Book a 15-minute chat to ask questions and learn
more about our programs.
Torilo Academy | Training Centre In Lagos, Nigeria
4.8Out of 5 stars














































































































































































































































































































































































































































































































Overall rating out of 111 Google reviews
Torilo Academy has been a great experience. Their practical approach to learning is excellent. The Tutors ensure all students are carried along.
This is the best Tech center so far
the experience has actually been electric
Learning at Torilo Academy has been great so far. Super nice tutors.
awesome tech school.
My experience at the academy has been perfect. Just what I expected
Amazing class on product design! Really enjoying my class so far
Very conducive space for learning with tutors ready to give their best.
I signed up for the Web Development course at Torilo Academy without having any prior knowledge about it and I can proudly say Torilo Academy has made the experience worth the while. I am now able to build functional and responsive websites, using HTML, CSS and WordPress. I'm glad I took the course...
I had an amazing experience. The instructors are ready and willing to help. A conducive environment, Free WiFi, interactive class. Thanks to the whole staff of Torilo. Mr Odunayo, Mr Ahmed, Mr Peter, Miss Gbemisola. You guys are awesome. Torilo Academy is the best place to be.
Torilo Academy is definitely your go to place for digital marketing. Within a space of 6 weeks, I was able to learn a lot about digital marketing. Teaching environment is very comfortable and the tutors are friendly.
Are you looking for a place to learn digital marketing, look no further. Torilo Academy is all you need, instructors are friendly, learning environment is conducive and they go all out with every little details. A big shout out to my instructor, Mr Peter Adetutu, you are awesome.
Words cant express the joy and fulfillment in my heart right now. Thanks to Torilo Academy my long time wish to have deep knowledge of digital marketing is accomplished. With very conducive learning environment, great instructors.....Torilo Academy is truly a place to be
Had a great and impactful time at Torilo. They are very professional, from my first enquire via phone call with the contact person Ayo to the facilitator Sam (awesome guy) always ready to listen and provide solution. It was worth every penny.
Torilo Academy is an excellent training institution for design courses. My time spent learning web design was worth it. Professional facilitators and conducive learning environment.
Torilo academy is the best place to learn digital marketing skills because they provide a conducive and comfortable learning environment, Mr. Peter Adetutu(digital marketing) is the best tutor I’ve come across and I’m extremely grateful to him. Learn digital skills at torilo academy and get that top notch quality learning .
The experience was a very great one. The teaching experience surpassed my expectations, well paced and thorough. I would advice/refer anyone to study at Torilo Academy.
Pay As You Learn
Focus on gaining practical skills and worry less about your payments.


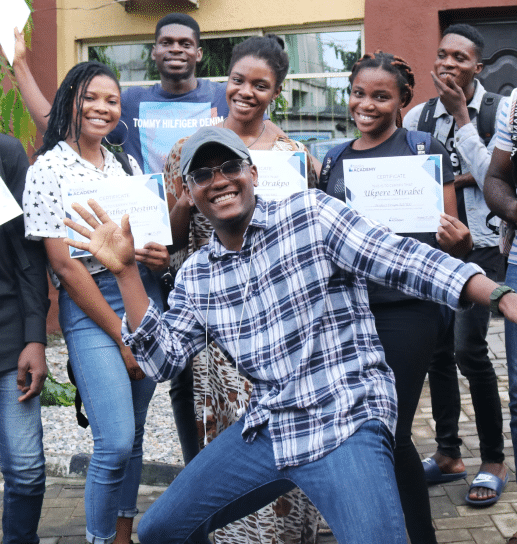
Passionate about a course?
We know how much you yearn to learn and advance to the next level of what the future holds for you. We have provided you with resources that makes persuading either your boss of relative easier. Take charge of your future now!
Creative and Collaborative Learning
Experience engaging and interactive sessions. At Torilo Academy training center, we leverage both group and individual sessions to ensure that our students practise working in teams and independently to build usable solutions.



